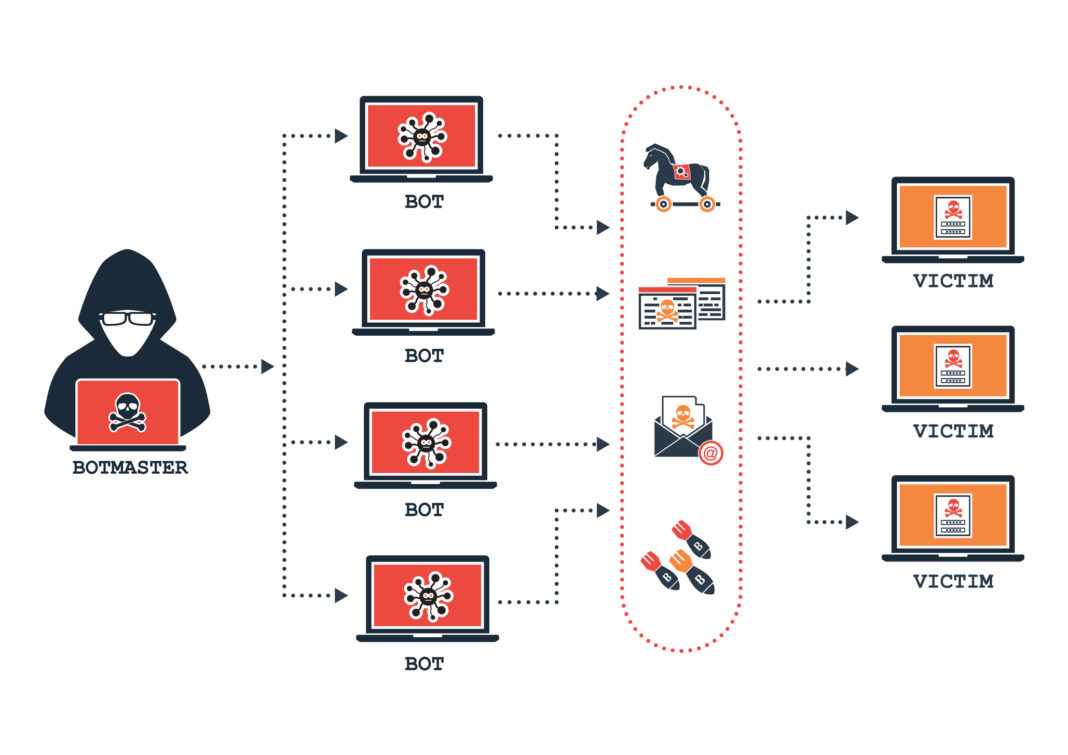
A botnet is a mashup of “robot” and “network.” Botnets are large-scale networks of infected computers controlled by one cyber attacker. Deploying malware, a hacker can harness remote control of thousands, even millions of individual devices, using their collective computing power to orchestrate a mass cyberattack from a centralized server.
An infected computer – or a bot – is sometimes called a zombie, and a botnet a zombie army. The zombie owner is likely unaware of its role in the botnet. Your PC, Mac, or Smartphone may continue to function, while the “bot-herder” directs the affected devices at a target. The kinds of cyberattack possible using a botnet includes online fraud, extortion, data theft, and DDoS attacks.
Bot-herders are not only agents of chaos. They also leverage botnets as communication channels. They command their bots to unwittingly launch spam to devices they interact with, infecting new devices and expanding the botnet. This unlocks an immense power and scope for a hacker conducting malicious attacks.
Why do they matter?
Botnets are a sophisticated and effective form of cybercrime. While malware can be deployed in discrete invasions, a botnet comprises brute force, swiftly targeting an organization in minutes, which is why it has emerged as one of the most prevalent modes of cyber attack over the past decade.
Botnets pose a powerful risk to individuals, enterprises, and government institutions. Locally, on your personal device, it may result in sluggish functionality and incessant popups. But the damage can be more extreme: high internet bills, stolen personal data, even grave legal implications from destructive activity originating from your device.
How can they be avoided?
While a botnet is an advanced cyber exploit, the defense methods are familiar; ensure you have up-to-date security software, avoid links and emails from unfamiliar sources, and consider subscribing to an advanced botnet detection and protection solution.
Key takeaways
- Botnets are a group of internet-connected devices managed by one, centralized server (a bot-herder).
- A bot-herder can directly infect a device, which then becomes a bot, or s/he can use an existing bot to expand the heist. So, your computer can become a botnet zombie through direct contact with the virus, or from normal communication with another zombie.
Oh, and the zombies likely think they’re acting totally normal. What virus?

- Ensure you have precautionary security measures installed and watch out for slowed internet performance, unexpected shutdowns, abnormal popups, and the inability to update your operating system.