We all like to look good on social media. Actually, I should say “we,” since I don’t participate much. But you know what I mean. Zits and other visual dings are Photoshopped, vacation photos go heavy on the glamor and light on the flight delays and leaky hotel toilets. But the most common flex is people who connect with strangers to make their social circle and following seem bigger than it is.
This last detail is a harmless ego trip for most social media users, but for hackers and scammers targeting their next victim it’s mission critical.
What is Profile Padding?
Profile padding is where a scammer, hacker or identity thief reaches out to new connections on social media accounts to seem “more real,” or, to the more vigilant user, less shady.
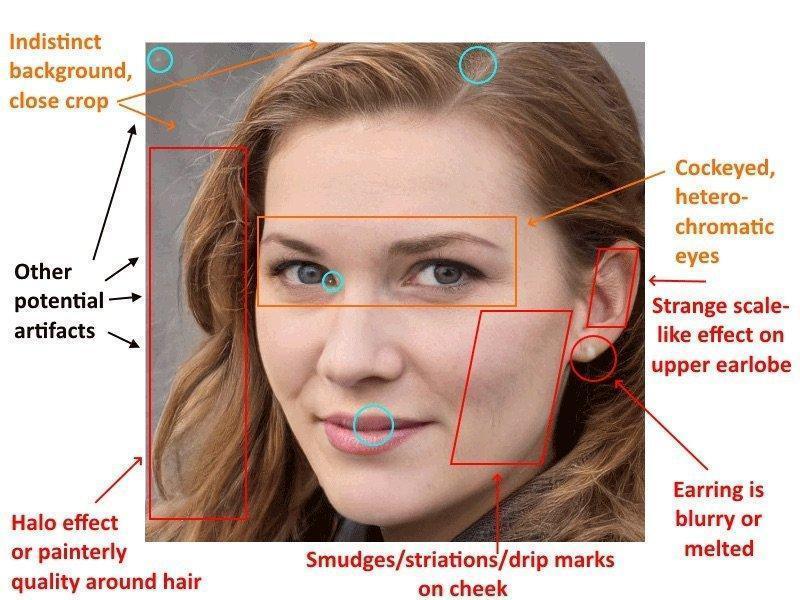
Katie Jones is an attractive 30-something whose LinkedIn profile boasted among other impressive milestones a fellowship at the Center for Strategic and International Studies, a well-regarded Washington D.C. think tank.
The problem was that Katie Jones didn’t exist. For starters, her resume didn’t check out. There was no record of her employment, or of her attendance at the University of Michigan. Additionally, her profile photo showed signs of deepfake technology at work. Her connections on LinkedIn, however, were both real and on point, including a senator’s aide, a deputy assistant secretary of state, employees at the Brookings Institution and Heritage Foundation, and economist Paul Winfree.
While the phantom Katie Jones was assumed to be part of an espionage campaign by Russian operatives (the Russians being no strangers to hacking), the technique is common among all stripes of scammers. If you send out bulk requests for connections on social media networks, you will eventually get at least a few people willing to add you to their networks. The more people on your networks, the more convincing your account is, ultimately leading to a seemingly verified and wholly synthetic identity.
While profile padding isn’t a crime in and of itself, it opens the door for a panoply of illegal activities.
A scammer could reach out to account holders with non-existent “business opportunities.” Alternately, s/he might focus on compiling enough user information to launch targeted spear phishing campaigns–a common way larger organizations are compromised. Too complicated? A malware-laden file attachment disguised as a resume or business inquiry can provide a tidy way in for cybercriminals.
Profile padding is easy, low-risk, and requires no investment other than time.
It’s also difficult to prevent profile padding activity, especially on professional-centric networks where the primary criteria for connections is a shared workplace or educational institution. Refusing or ignoring an invitation to connect from an unfamiliar colleague could cause offense, which most of us want to avoid.
Recruiters and salespeople also frequently send unsolicited invitations to connect, which further blurs the line between a “real” connection and a padded one.
What Can Be Done?
- Be selective: This is easier said than done, especially in industries where having a large network and online presence is advantageous. Every new connection represents an increase in your attackable surface. Be careful when accepting invitations or communicating with unfamiliar people online. At a minimum, your reputation may be providing cover and legitimacy to a scammer.
- Learn to spot deepfakes or compromised accounts: The profile picture of Katie Jones looked convincing at first glance, but a closer look revealed some telltale signs including uneven heterochromatic eyes, a strangely blurred earring, and digital artifacts in the photo subject’s hair, eyes and ears. Services such as Google reverse image search can quickly show if there are multiple names or identities associated with a profile photo.
- Take a moment to check out a connection request’s identity: This can ferret out suspicious accounts.
- Don’t overshare on social media: Personal information and data can present a goldmine for cybercriminals, especially when they’re able to see your account from the “friend” or trusted contact digital viewpoint. The more details of your life or career you share, the easier it is to gain access to accounts and sensitive data. Keep information including birthdays, names of relatives, exact locations and travel plans and the like off of any public forum.










