The field of cybersecurity testing is riddled with double-edged swords. There are innumerable tools used by cybersecurity professionals to help identify vulnerability at an organization that can be used by cybercriminals to target victims. .
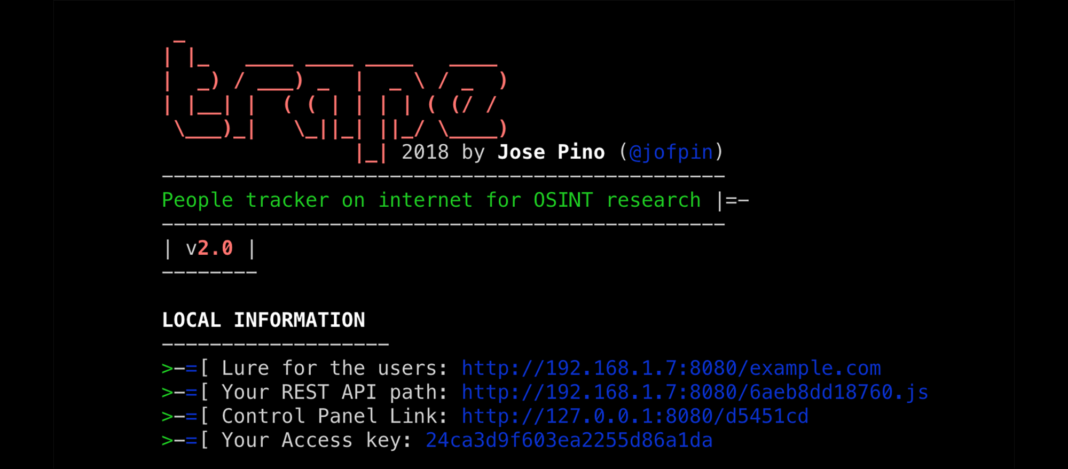
Trape dates back to 2018. It is a software program originally developed to perform penetration testing and open-source intelligence (OSINT.) Trape is a good example of the double-edge sword problem. Freely available for download and easy to deploy, Trape generates a clone of any website online and then directs social engineering and hacking related activity at it.
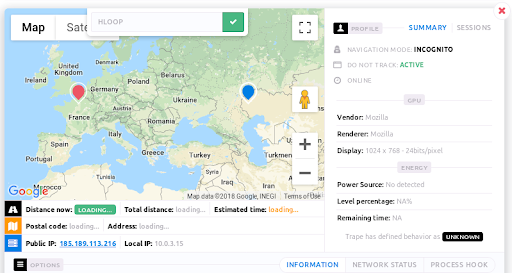
Trape’s interface is simple. The user enters the URL of the site they want to clone. Trape then generates a perfect copy of the site at a new decoy address. As soon as a user opens the cloned website, Trape is able to identify their location, IP address, and access browser information including any websites or services they’re logged into.
Trape can also send code to a target’s browser (allowing them to log keystrokes or intercept account credentials). It launches phishing attacks, sends malicious files to be downloaded and more.
Trape requires a visit to a cloned URL, but an address could be disguised as a QR code or a minified web address posted to social media. It can also, of course, be sent in a phishing email.
Despite the obvious potential for Trape to be misused, its developers maintain that the program is meant to educate people about the pervasiveness of online tracking.
“We are totally convinced that if we teach how vulnerable things really are, we can make the Internet a safer place,” reads the project disclaimer on GitHub.
Takeaways:
- Always double-check the URL of a site before clicking a link.
- Use QR codes with extreme caution, and only from trusted sources.
- Browse the web in incognito mode to block unintentionally shared information about other accounts and services.
- Avoid link shortening services that can be used to direct victims to cloned websites.