Most phishing campaigns are designed to steal credentials. They rely on social engineering rather than high-tech methods–getting a target to click a link using scare tactics, clicky bait, and otherwise monetizing user distraction.
When we’re paying attention, most of us are pretty good at spotting the telltale signs of a cloned website and the ubiquitous phishing emails that regularly come our way. The signs are many, including misspelled URLs or domain names, email addresses that don’t match the sender, logos that don’t look quite right.
A new approach to stealing credentials overcomes this weakness. Browser-in-browser attacks send targets to a page that looks like a browser page. It is in fact an exact replica of the browser that the user thinks they’ve navigated to. The scam page sits in the actual browser window with what seems like a legitimate URL, one that relies on an easy-to-overlook difference or something even more devious.
It is not a browser, but it looks like one. Users do not realize they’ve been diverted into enemy territory, and enter credentials.
Here’s how it works:
Browser-in-the browser attacks, or BitB start with a target clicking on what looks like a legitimate link in an email. This is easier than it sounds; the following link says “https://adamlevin.com” but directs instead to loudtreemedia.com. Here’s a look at how the code works:
<a href=”https://loudtreemedia.com”>https://adamlevin.com</a>
The URL between the quotation marks is the actual destination for the link.
An attacker can also cover their tracks by using URL shorteners such as Bit.ly to obscure the link’s actual destination. As many email services use URL aliases and shorteners as a means of collecting user activity, this would be unlikely to draw suspicion.
Once the phishing page has loaded, a user is presented with an option to login. To avoid needing to manage passwords, many users now opt for what’s called third-party single sign-on (SSO), where they enter credentials for their Google, Apple or Facebook accounts to authenticate themselves on other websites. This is where the BiTB trick comes into play.
When the target mouses over the link to login with a Google account, the link displayed as the destination looks like the legitimate URL for Google accounts: https://accounts.google.com/ServiceLogin/
The BiTB script overrides the link using a relatively simple script triggering a popup instead of taking them to a legitimate page. The popup is a clone of the page, but it displays the proper URL, and the script perfectly imitates a separate browser window that can be dragged around the screen, closed, and conforms outwardly to the browser and operating system used by the target. (See the screenshot below or a demo here – Source: https://mrd0x.com/)
Once the account credentials to Google, Facebook or Apple have been captured, the hacker then has a skeleton key to multiple websites and services connected to this account with their target none the wiser.
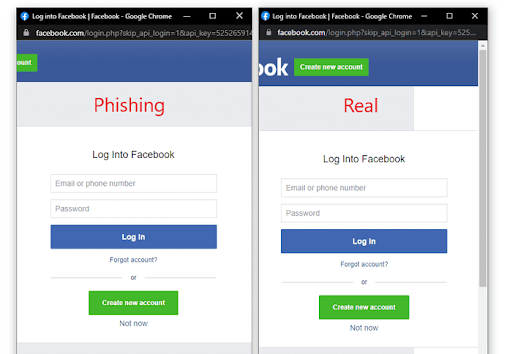
How to protect against BiTB attacks:
- Be careful where you click: BiTB attacks still require an initial click on a malicious link. Treat any incoming emails or messages as potentially dangerous.
- Drag popup login windows to the edge of your screen: One recognizable difference between an actual popup and a BiTB popup window is that an actual browser window can be moved off the edge of the screen. A BiTB popup is part of the parent webpage and cannot be moved past its boundaries on a desktop browser.
- Enable 2-Factor authentication: Enabling 2-Factor authentication on your accounts, especially those that you use for SSO services, limits the effectiveness of BiTB attacks. Having your login and password is less useful to a hacker if they still need your mobile device to login.
- Consider a password manager or email alias services instead of using SSO: SSOs help to cut down on the number of passwords you need to use, but you’re trading security and privacy for convenience. Once your Google, Facebook or Apple credentials are compromised online, your attackable surface increases considerably.
If you are privacy-minded, you may also want to consider that SSO provides the host companies sensitive and detailed information about your browsing habits. Good password hygiene and a well-reviewed password management service will render this scam ineffective.










