Get in Touch
The more you can do to safeguard your company against cyberattacks and employee error, the better you will fare in the coming years. Cyber...
If you are moving fast as we tend to do during the workday, the following four web addresses may not look so different from...
Video conferencing platform Zoom has been crowded with the spread of the Covid-19 pandemic and the adoption of social distancing measures.
Criminal cyber activity has...
Marriott International announced a data breach that may have exposed the information of 5.2 million guests. Among the information potentially compromised are names, birthdates,...
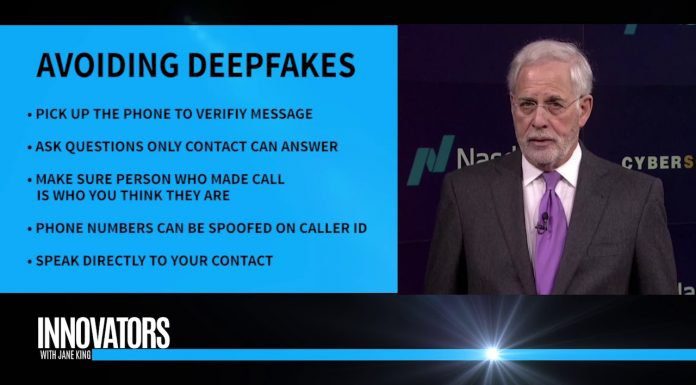
In the latest episode of Third Certainty, Adam Levin explains the danger of voice deepfakes.
Businesses across the country have had to adjust to their employees working from home. For many it was a last-minute scramble to adjust to what has become...
Researchers at the cybersecurity firm Sucuri have uncovered a new set of e-skimming attacks targeting websites using the WordPress WooCommerce e-commerce plugin.
E-skimming attacks typically...
The Covid-19 pandemic created an opportunity for hackers to target the newly remote workforce. Hospitals have been targeted by ransomware (despite initial assurances to...
Two critical zero-day exploits for the Zoom video conferencing platform just hit the market.
The alleged exploits take advantage of vulnerabilities in Zoom’s Windows and...
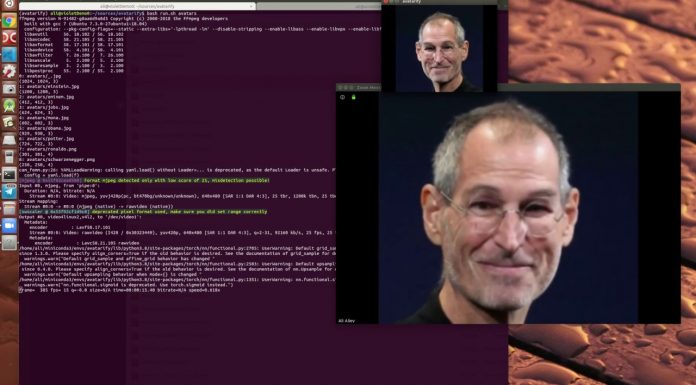
A newly released program allows users to create real-time deepfakes on video conferencing platforms including Zoom, and Skype.
Avatarify is an open-source program that can...