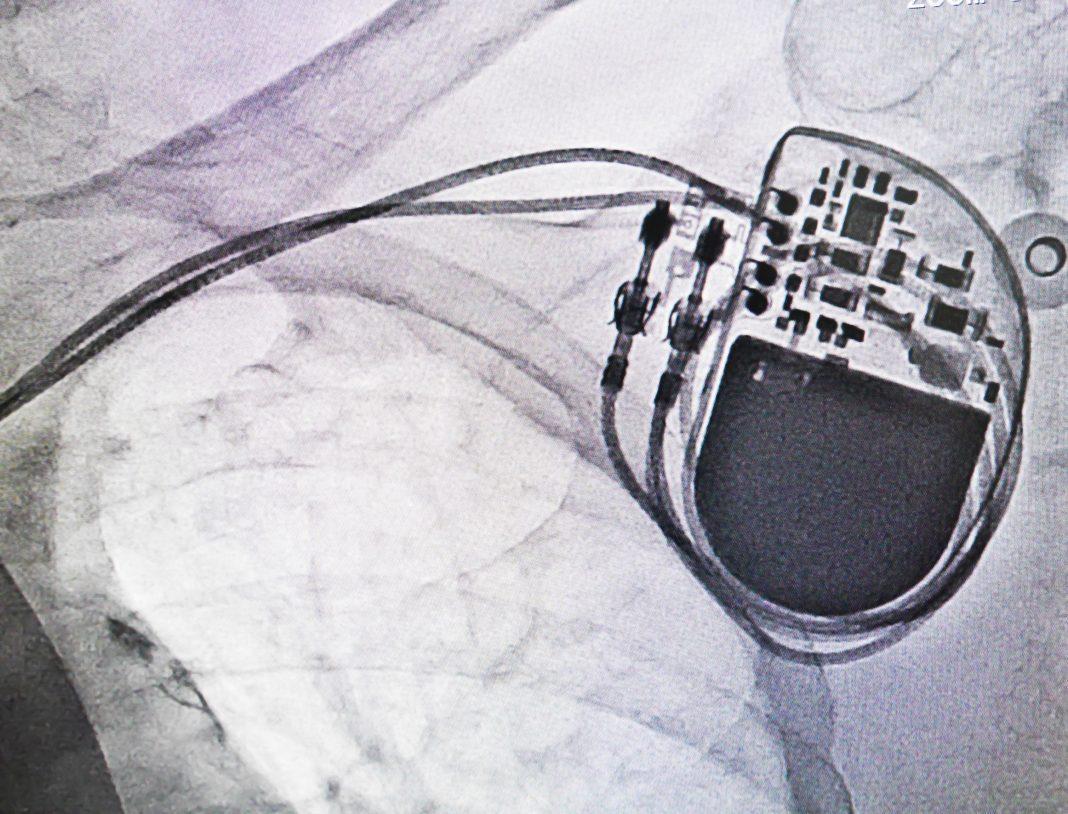
Security researchers at the recent Black Hat and Def Con security conferences in Las Vegas have placed malware on pacemakers as a proof-of-concept hack to highlight the potential for security vulnerabilities in IoT-enabled medical devices. Another separate demonstration revealed that patients’ vital signs could be falsified in real time.
The malware attack on IoT medical devices made it possible for a hacker to deliver shocks to a target’s heart via an unencrypted connection, and as such represents a new and potentially life-threatening vector for hackers.
Medtronic manufactures the targeted pacemakers. The company has come under fire from security experts for their response to the news of their device’s vulnerability. Also criticized was Medtronic’s failure to implement rudimentary security standards such as https encryption and digital signatures.
The researchers from cybersecurity agencies WhiteScope and QED Secure Solutions demonstrated that there were two ways to perform the hacks; the first uses a known vulnerability on Medtronic’s own network, and the second exploits the update process for the medical hardware itself. Researchers were also able to display a potential hack on a Medtronic insulin pump that was running outdated software.
Neither pacemaker nor the insulin pump in question have been hacked outside of a research setting, so the vulnerabilities remain strictly proof of concept, but both serve to highlight the potentially disastrous consequences of internet-enabled medical equipment.
Hacking vital signs in real time could lead to life-threatening mistakes by way of misdiagnosis, or the administration of the wrong treatments and/or medications.
Doug McKee, senior security researcher at McAfee’s Advanced Threat Research team, demonstrated a “weakness in the RWHAT protocol, one of the networking protocols used by medical devices to monitor a patient’s condition.” The weakness could be used to present healthcare providers with erroneous information that could lead to deadly mistakes. The flaws, McKee pointed out, would be preventable with proper security, such as encryption and tighter authentication protocols.
Read more here.