You couldn’t go a week last year without seeing a ransomware headline in the news. And it wasn’t because the media paid more attention to this relative newcomer in the area of cybercrime. Ransomware attacks on businesses skyrocketed 365 percent in 2019, and all signs point to more of the same in 2020.
As bad as the ransomware scourge was for businesses, local governments arguably had it worse. Baltimore, Atlanta, and Akron, Ohio, were among the bigger cities hit, followed shortly thereafter by Lake City and Riviera Beach in Florida, and then a coordinated campaign against 22 Texas municipalities. New Orleans was hit later on in the year, and still hasn’t completely restored its data and services.
While the number of ransomware attacks is enough to make even the calmest among us want to hide in a panic room, the likelihood of such attacks slowing down is right up there with the chance that President Trump will be asking U.S. attorney for the Southern District of New York Geoffrey Berman to prepare his tax return this year.
We can’t hide from the threat. Cybersecurity experts are aligned on this point: Ransomware is a serious issue. The situation is not going to be magically resolved. But while it’s worked on, there’s something all of us can do. Businesses, individuals, governments, and organizations alike can become savvier about the threat, understand the scope of the problem, and prepare for it.
What Is Ransomware?
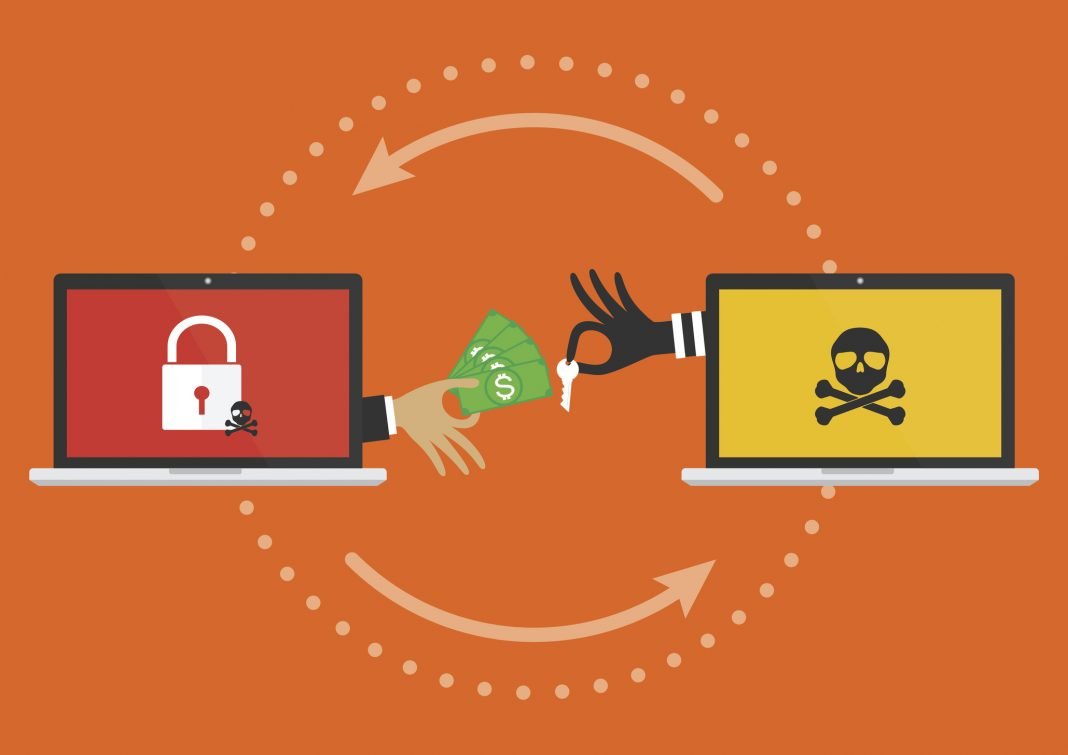
While the sophistication and methods of attack may vary, the short answer is that ransomware is a type of malware that encrypts critical data on a computer or computer network so that users can’t regain access without paying a “ransom.” The payment is typically demanded in bitcoin, because it’s difficult to trace and easily transferable. Upon payment the hacker, if “honest,” will provide a digital key to decrypt the information. It doesn’t always go down that way. In fact, the criminal may leave the data encrypted after stealing it and put it up for sale on the dark web or simply use it in the commission of a crime.
Sometimes, these clowns don’t even know how to decrypt the data. Hackers aren’t generally focused on providing competent customer service. It’s all about the payday.
What makes ransomware such a difficult vector to recover from is the encryption, which ironically continues to be one of the best methods of securing data from hackers. In effect, ransomware is the weaponization of a cyber-protection protocol.
The threats used to get payment are serious, starting with the possibility that the data will be encrypted permanently. Few organizations can survive the loss of all (or even a significant portion of) their data. Hackers often threaten to delete the data by a certain deadline, or as is becoming more common, they may opt to release the data to the general public, which is a variant attack known as extortionware.
While there have been some success stories when it comes to ransomware remediation, the odds are not in your favor. The safest bet is to prevent these attacks in the first place. But there have been informative examples of companies that mitigated the damage from a ransomware attack. Your Cliffs Notes version: Put yourself in a position where you can’t be affected by such a hack.
Back Up Everything: Data recovery is an expensive and time-consuming process even when it isn’t being done in the wake of a ransomware attack. If the loss of your data is potentially catastrophic, the most straightforward solution is to back up your systems and data and do it often. Bear in mind that your data backups will be of no use if they are also encrypted by a ransomware attack, so keep them stored separately and offline.
Call for Help: The odds are very good that your IT staff is already overworked as a result of their day-to-day operations. Part of this can be blamed on the lack of cybersecurity skills available in the workforce. A recent study found that the cyber gap impacts 74 percent of organizations, with 63 percent of cybersecurity professionals reporting that the talent gap increased their workload, 68 percent reporting negative effects on their personal lives, and 38 percent reporting higher burnout rates.
The types of threats are ever changing, adding to the challenge cybersecurity professionals face. Phishing attacks, unpatched software vulnerabilities, and ransomware attacks all amount to an exercise of futility. If you expect your existing staff to be able to resolve a ransomware attack with the resources at their disposal, think again. They can’t do it. Find a contractor that specializes in ransomware recovery before you’re hit.
Silo Your Data: While the New Orleans ransomware attack was an unmitigated disaster for the city, one thing that helped was that it didn’t take their emergency services offline: police, paramedics, and fire departments were still able to respond to calls, because they were on a separate system from the compromised city services. Consider taking the same approach: Run and maintain separate servers and storage for your data. While it may require more resources in the short term, doing this will greatly aid in the containment of the damage from a ransomware attack.
Get Covered: I’ve said it before and I’ll say it again: Cyberattacks and data breaches have become the third certainty in life after death and taxes. With the constant threat of cyberattacks, foreign threat actors, ransomware-as-a-service operators, disgruntled former employees, and just plain misconfigured servers, insuring your company against cyber-risk is and should be viewed as a basic requirement of doing business.
Case in point: The Heritage Company went out of business following an October 2019 ransomware incident, leaving 300 employees out of work shortly before Christmas. Don’t be the next Heritage Company. If your company already has cyber insurance coverage, consider increasing it. Both New Orleans and Baltimore opted to increase their limits after discovering that the recovery process cost significantly more than was covered.
The unfortunate reality here is that the ransomware epidemic is likely to worsen before it improves. The best defense is to practice good cyber hygiene, back up data, keep systems patched and up-to-date, and invest in workplace training to identify phishing emails and other suspicious behavior. But if that fails, it’s wise to have a response plan in place.