Get in Touch
Hackers successfully breached the servers of a popular blogging platform and used them to mine cryptocurrency.
Ghost, a Singapore-based blogging platform with 2,000,000 installations and 750,000 active users, announced that hackers had breached their systems.
"The mining attempt... quickly overloaded most of our systems which alerted us to the issue immediately," the company announced May 3, adding that “here is no...
Cybercriminals are actively targeting Covid-19 hotspots with malware and phishing campaigns, according to a new report from Bitdefender.
The report, “Coronavirus-themed Threat Reports Haven’t Flattened the Curve,” shows a direct correlation between confirmed Covid-19 cases and malware attacks exploiting the crisis.
These findings confirm a similar report that showed a 30000% increase in Covid-19-themed attacks from January to March.
“Countries that have...
For the last few years, cybersecurity experts have been sounding the alarm on something called e-skimming. In this kind of attack, hackers intercept payment card data and personal information from e-commerce sites by exploiting the architectural complexity of those e-commerce sites.
While there have been several major breaches that were the result of e-skimming, including Macy’s and British Airways, the...
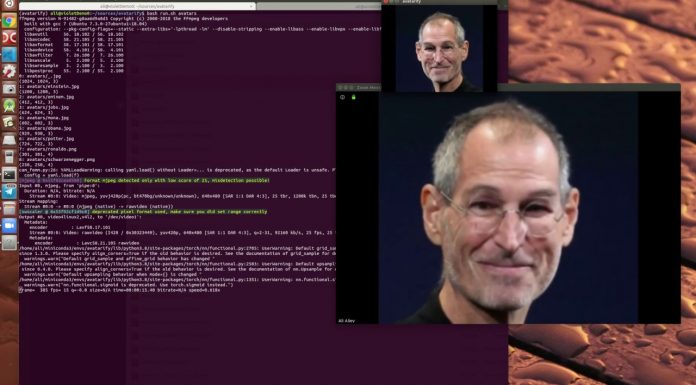
A newly released program allows users to create real-time deepfakes on video conferencing platforms including Zoom, and Skype.
Avatarify is an open-source program that can instantly transform the appearance of users during a video conference. Its developer, Ali Aliev, unveiled the software earlier this month on Youtube where he swapped his face with the likes of Steve Jobs, Eminem, Albert...
Two critical zero-day exploits for the Zoom video conferencing platform just hit the market.
The alleged exploits take advantage of vulnerabilities in Zoom’s Windows and MacOS applications, allowing hackers to spy on calls, and in some cases, take control of Windows machines.
Zero-day exploits are vulnerabilities that are discovered by hackers before they can be identified and patched by software companies,...
The Covid-19 pandemic created an opportunity for hackers to target the newly remote workforce. Hospitals have been targeted by ransomware (despite initial assurances to the contrary), phishing scams are using pandemic-related scare tactics, and video conferencing apps have become the new go-to for everything from domain-spoofing attacks to zoombombing. Even NASA has reported a 100% increase in phishing and...
Researchers at the cybersecurity firm Sucuri have uncovered a new set of e-skimming attacks targeting websites using the WordPress WooCommerce e-commerce plugin.
E-skimming attacks typically use injected code on websites to intercept customer data as it is being entered by customers. This allows hackers to bypass otherwise secure encryption and steal credit card and personal information.
The best-known e-skimming campaigns have...
Businesses across the country have had to adjust to their employees working from home. For many it was a last-minute scramble to adjust to what has become "the new normal" in the face of the coronavirus pandemic.
As businesses and their employees settle into what could be for many a span of several weeks or months with a mandatory or recommended work from home...
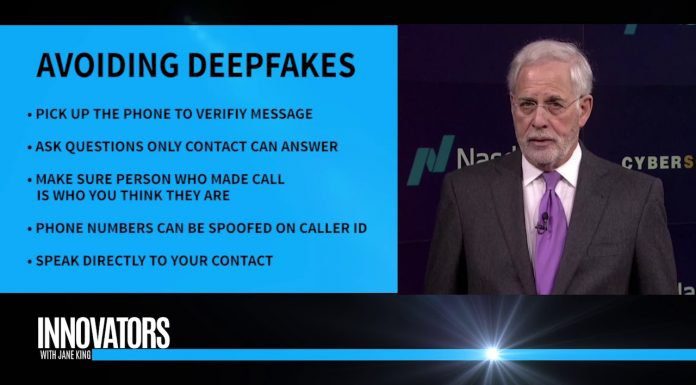
In the latest episode of Third Certainty, Adam Levin explains the danger of voice deepfakes.
Marriott International announced a data breach that may have exposed the information of 5.2 million guests. Among the information potentially compromised are names, birthdates, mailing addresses, phone numbers, email addresses, and birthdates.
This is the second major data breach that Marriott has experienced in recent years; in 2018, the company announced that the information of 327 million customers of subsidiary...