Get in Touch
Protecting Retirement Accounts – Third Certainty #10
In the tenth episode of Third Certainty, Adam Levin explains how to protect retirement and financial accounts against takeovers by scammers.
Mitsubishi Electric Discloses Major Data Breach
Mitsubishi Electric Corporation announced that it experienced a major data breach in June 2019 that has been traced back to a Chinese hacking group.
“ur...
The 2020 Tax Frauds: Old is New and “Better” than Ever
This tax season it’s the same old story when it comes to fraud; but the 2020 reboot is going to require tax professionals and...
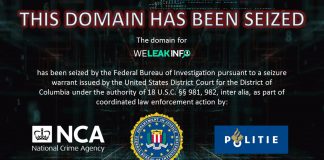
FBI Shuts Down Website Trafficking in Breached Data
The FBI has seized the domain of WeLeakInfo.com, an online service that sold data from hacked and breached websites.
The domain seizure and termination of...
Baby App “Peekaboo” Leaks Photos, Videos and Personal Data
An unsecured database discovered online has leaked thousands of baby photos and videos.
Bithouse, Inc. left unprotected and accessible online an Elasticsearch database containing nearly...
Las Vegas Successfully Averted a Cyberattack
The City of Las Vegas successfully averted what could have been a disastrous cyberattack earlier this month.
City officials detected a cyberattack January 7, and...
Currency Exchange Company Travelex Hit By Ransomware Attack
Currency exchange giant Travelex has effectively been taken offline by a ransomware attack.
The attack was first detected the night of December 31. Soon after,...
U.S. Federal Website Defaced by Pro-Iranian Hackers
A federal website was defaced with pro-Iranian messaging in what is believed to be retaliation for the U.S. drone strike that killed one of...
What’s In Your Business Plan? California’s Privacy Law Goes Into Effect
California’s groundbreaking privacy law went into effect January 1, 2020.
The California Consumer Privacy Act (CCPA) requires businesses to inform state residents if their data...
The United Kingdom Leaks Home Addresses of Prominent Brits
2020 seems to be getting off to an inauspicious start with the compromise of the home addresses of prominent UK citizens--many of them in...